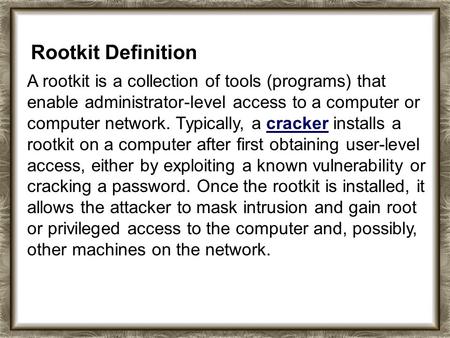
KRK SYSTEMS - Studio Monitors, Headphones, Subwoofers, Speakers, Monitoring Applications and Room Correction Technology

KRK SYSTEMS - Studio Monitors, Headphones, Subwoofers, Speakers, Monitoring Applications and Room Correction Technology

Protect Against Rootkit and Bootkit Malware in Systems that Boot from External SPI Flash Memory | Microchip Technology | Microchip Technology

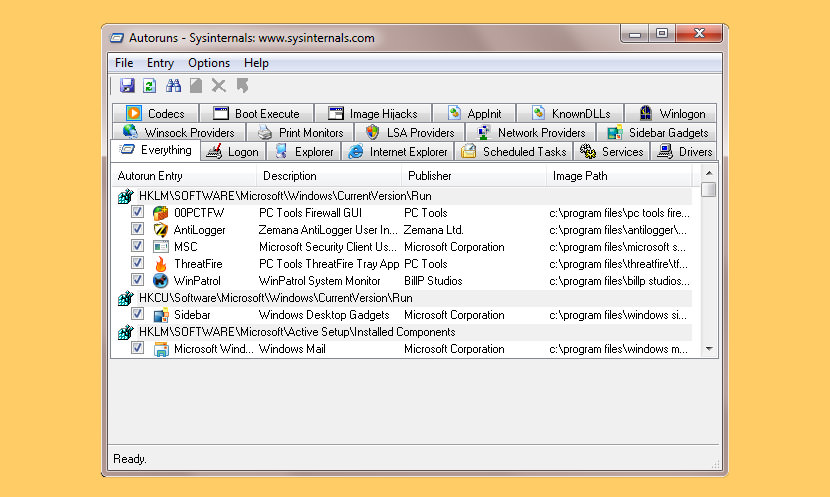
Architecture of Volatile Kernel Rootkit Hidden Process Detection View... | Download Scientific Diagram